It's was about a year ago, someone in my rather big office (100~200 people) started to send annoying emails with cheesy phrases and images regarding the new year resolutions.
These emails were sent from a made-up gmail account.
I've realized that this will be a good opportunity to test the privacy issues of WebRTC and to find out who is this despicable person.
As you probably already know - WebRTC has this flaw/feature which allows a website to reveal your local IP address. Check it out.
So I made up this quick website with some new-year resolutions images I found on the first page result in Google. Used one of my best domain name with valid HTTPS.
Waited till that horrible person will send a "funny" message which is intended directly at me and replied:
"LoL that was soooo funny, checkout this website with the funniest new year resolutions". Now, if you'll go to this website (now with different domain) it'll send me an email titled "The fish is in the net" with your local IP address.
That doesn't mean much for you, but for that person it means I'll know who he is.
Everything was setup perfectly, I set down and waited for that email. Yet... nothing happened there was no click. That was a bummer but I didn't give up.
As in all successful physhing attacks - it's important who the message is coming from. So I made up a new message with a new link and asked someone with more prestige in the company, AKA a manager, to send it. And it worked!!!
I now had the precious local IP.
Getting the hostname from this IP is easy using nmap --system-dns <ip> or nslookup <ip> on Windows.
Since it's a big company the hostname is some kind of generated serial which doesn't give much information.
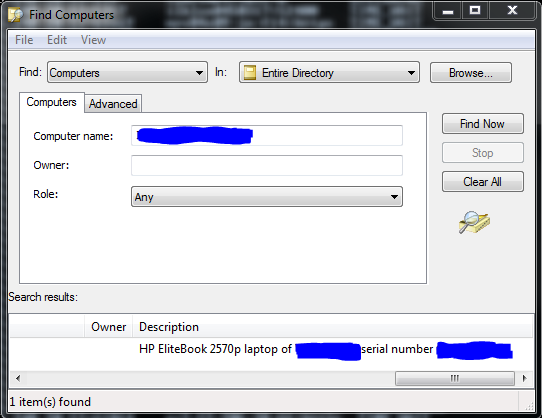
Luckily searching the Active Directory is too damn easy.
Busted!!!
So we found him... that despicible person... finally... actually he's a nice dude ;)
The website is still here https://localip.herokuapp.com/
Code is here https://github.com/guy-a/localip